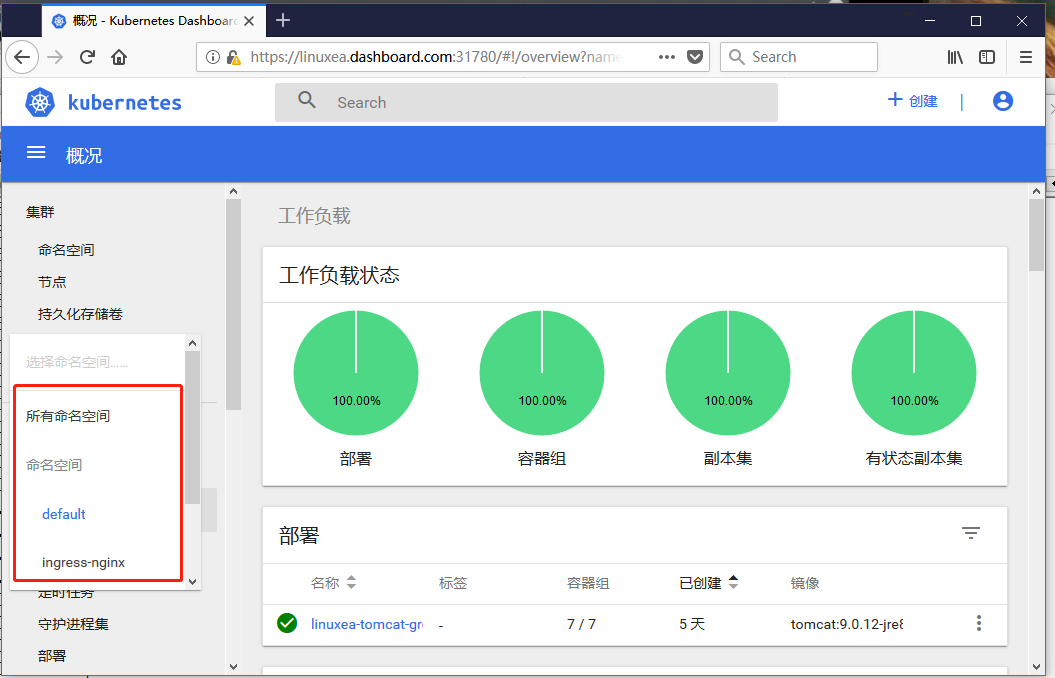
dashboard也是做为kubernetes核心附件存在,这种附件还有就是作为名称解析和服务发现的coredns,通常系统部署后会自动安装。Dashboard在新的版本里面有这复杂的权限检查机制
在使用kubeadm安装的RBAC默认强制启用的,而Dashboard接口是管理整个集群的接口,认证管理的方式类似于“自我认证”。 它类似于kubernetes集群UI前段,认证也是kubernetes的用户的认证。在登录Dashboard的用户名和密码一定是kubernetes中存在的,这也就是说Dashboard本身并不做认证,仅仅做认证代理(认证代理在之前提到过,Dashboard作为porxy与k8s认证)。所有的账号认证和授权都是kubernetes之上的。
Dashboard展示k8s之上的大部分资源状况,如:名称空间,自动发现,分级授权,pod信息等。
部署#
我们通过github上的Dashboard的getting-started在线进行安装
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/master/src/deploy/recommended/kubernetes-dashboard.yaml
[marksugar@linuxea role]# kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/master/src/deploy/recommended/kubernetes-dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
会很快的下载完成,并且run,在这个yaml文件中定义了之前所述的一些role角色的权限以及pod等,可进行查看。
Dashboard属于kube-system资源,使用kubectl get pods -n kube-system查看
[marksugar@linuxea role]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
kubernetes-dashboard-767dc7d4d-srfm2 1/1 Running 0 50s
在yaml中, Dashboard Service 是通过443向外提供服务,并且是clusterIP的type
[marksugar@linuxea role]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP 20d
kubernetes-dashboard ClusterIP 10.101.13.145 <none> 443/TCP 32m
通过打补丁的方式修改kubernetes-dashboard的type为NodePort类型,之后就可以通过集群内的节点访问
[marksugar@linuxea role]# kubectl patch svc kubernetes-dashboard -p'{"spec":{"type":"NodePort"}}' -n kube-system
service/kubernetes-dashboard patched
使用kubectl get svc -n kube-system查看端口,没有指定就会随机,如下随机端口30142
[marksugar@linuxea role]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP 20d
kubernetes-dashboard NodePort 10.101.13.145 <none> 443:30142/TCP 1h
我们通过30142在任一一台node访问,通过https://NODEIP:30142访问,如下:
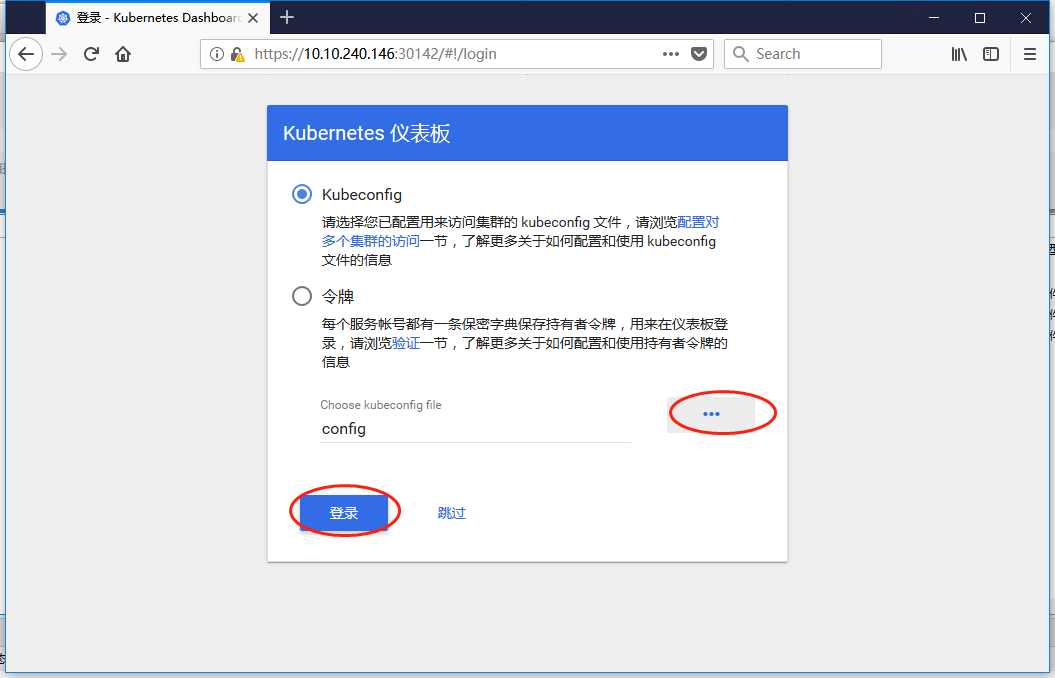
认证的账号必须是ServiceAccount,以供被Dashboard pod对kuberntes进行认证,支持config和token.
创建dashboard用户#
1,切换到/etc/kubernetes/pki/目录下,创建一个专用的证书,先生产一个私钥
[marksugar@linuxea role]# cd /etc/kubernetes/pki/
[marksugar@linuxea pki]# (umask 077; openssl genrsa -out dashboard.key 2048)
Generating RSA private key, 2048 bit long modulus
..........+++
.............+++
e is 65537 (0x10001)
2,使用api server的ca生成一个证书签署请求
如果使用域名访问,这里需要填写域名CN=linuxea.dashboard.com
[marksugar@linuxea pki]# openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=linuxea/CN=linuxea.dashboard.com"
开始签署
[marksugar@linuxea pki]# openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 365
Signature ok
subject=/O=linuxea/CN=linuxea.dashboard.com
Getting CA Private Key
3,创建secret
将生成的私钥和证书创建secret的tls类型的证书。但是由于dashboard作为一个应用程序,要在应用程序中使用,就需要创建成generic
[marksugar@linuxea pki]# kubectl create secret generic dashboard-cret -n kube-system --from-file=dashboard.crt=./dashboard.crt --from-file=dashboard.key=./dashboard.key
secret/dashboard-cret created
[marksugar@linuxea pki]# kubectl get secret -n kube-system|grep c-cret
dashboard-cret Opaque 2 18s
token认证#
在之前我们知道,dashboard作为一个pod,与api server交互就需要向kubernetes认证才能有权限。
那就需要一个serviceaccount链接kubernetes。其中根据不同的权限绑定合理的role,或者clusterrole
1,在集群创建一个serviceaccount,名称是dashboard-admin,这个作为集群管理
[marksugar@linuxea pki]# kubectl create serviceaccount dashboard-admin -n kube-system
serviceaccount/dashboard-admin created
[marksugar@linuxea pki]#
[marksugar@linuxea pki]# kubectl get sa -n kube-system |grep dashboard
dashboard-admin 1 25s
2,通过clusterrolebinding把dashboard-admin和集群管理员建立绑定关系
创建一个名称为dashboard-cluster-linuxea的clusterrolebinding
--clusterrole=cluster-admin 默认的集群管理员,这里指定名称空间,既所有名称空间的权限
--serviceaccount=kube-system:dashboard-admin左边kube-system是名称空间,右边是serviceaccount名称
[marksugar@linuxea pki]# kubectl create clusterrolebinding dashboard-cluster-linuxea --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-linuxea created
[marksugar@linuxea pki]# kubectl get clusterrolebinding |grep linuxea
dashboard-cluster-linuxea 1m
这些绑定完成就能获取对应的serviceaccount的secret信息,并且通过secret访问集群。这个secret是自动生成的,如下:
[marksugar@linuxea pki]# kubectl get secret -n kube-system |grep admin
dashboard-admin-token-vc7cv kubernetes.io/service-account-token 3 16m
3,我们查看这个kube-system名称空间dashboard-admin-token-vc7cv的secret的详情,其中的token就是我们要的认证信息,使用这个token登陆
[marksugar@linuxea pki]# kubectl describe secret dashboard-admin-token-vc7cv -n kube-system
Name: dashboard-admin-token-vc7cv
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name=dashboard-admin
kubernetes.io/service-account.uid=dfe5cdaf-c9f3-11e8-a8ab-88882fbd1028
Type: kubernetes.io/service-account-token
Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdmM3Y3YiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZGZlNWNkYWYtYzlmMy0xMWU4LWE4YWItODg4ODJmYmQxMDI4Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.qcPhHAkyW0k5gdkkDaTD-DVxRcrZ5Ml_Kcxw0mZIYlJWME_1Wu1_i4B9jE1RcwKDZHV0ND8jpN91oUg1Ac8O6X8VwsfpFw1HzcBv7Te46L4_Z2NjIBuf6cPngkHx1Ija08_BLUd--i3E9cJrTsrqaZojr1JO4ZTHifU7K6cKpGUmbvbYjkIASzj8onT2988znkjp13bvdx7YF3hrKMg4jeDFbR-yMPEwXadgiY0IHArekzLuL37KiRVGgEubuqZFy7fkBPiSQGWc9ecl5dwhmhfofHm7WuKlf4Lvwyz3ivGqPFuoKk0AMmAME3ULOO7INaTlRQkSGJs-bdWl7y-eIg
ca.crt: 1025 bytes
namespace: 11 bytes
[marksugar@linuxea pki]#
4,安装,并且打补丁修改type类型
[marksugar@linuxea pki]# kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/master/src/deploy/recommended/kubernetes-dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
[marksugar@linuxea pki]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP 21d
kubernetes-dashboard ClusterIP 10.101.194.113 <none> 443/TCP 3s
[marksugar@linuxea pki]# kubectl patch svc kubernetes-dashboard -p'{"spec":{"type":"NodePort"}}' -n kube-system
service/kubernetes-dashboard patched
这里的端口变成了31780,而后直接用node加31780访问
[marksugar@linuxea pki]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP 21d
kubernetes-dashboard NodePort 10.101.194.113 <none> 443:31780/TCP 18s
[marksugar@linuxea pki]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
kubernetes-dashboard-767dc7d4d-56hk4 1/1 Running 0 5m
登陆成功。可以对其中的所有配置进行修改,删除等操作,权限非常大。这里有可以使用https://linuxea.dashboard.com:31780进行打开
但是这样的密码无疑太长了
token部分权限控制#
此刻我只需要给一个账号某一些权限,如delfault。或者我只想给部分权限,那么也可以做的。
创建一个名称为linuxea-default的serviceaccount,namespace限制为default
[marksugar@linuxea pki]# kubectl create serviceaccount linuxea-default -n default
serviceaccount/linuxea-default created
创建一个rolebinding名称为linuxea-default,绑定到clusterrole的admin,那这就意味着对集群内的default名称空间有管理权限
[marksugar@linuxea pki]# kubectl create rolebinding linuxea-default --clusterrole=admin --serviceaccount=default:linuxea-default
rolebinding.rbac.authorization.k8s.io/linuxea-default created
而后拿出token登陆
[marksugar@linuxea pki]# kubectl get secret
NAME TYPE DATA AGE
admin-linuxea-token-4zpzk kubernetes.io/service-account-token 3 4d
default-token-k25gj kubernetes.io/service-account-token 3 21d
linuxea-default-token-zpjqr kubernetes.io/service-account-token 3 3m
redis-passwd Opaque 1 8d
tomcat-ingress-secret kubernetes.io/tls 2 5d
[marksugar@linuxea pki]# kubectl describe secret linuxea-default-token-zpjqr
Name: linuxea-default-token-zpjqr
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name=linuxea-default
kubernetes.io/service-account.uid=7185bafa-c9f9-11e8-a8ab-88882fbd1028
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImxpbnV4ZWEtZGVmYXVsdC10b2tlbi16cGpxciIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJsaW51eGVhLWRlZmF1bHQiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI3MTg1YmFmYS1jOWY5LTExZTgtYThhYi04ODg4MmZiZDEwMjgiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpsaW51eGVhLWRlZmF1bHQifQ.LEJqExx_-zl_7slc46aEWoRnD1zxvxmITYn0ZA-GBvdwYReICzy0dPCi4E-CxA1I3VLtmcogmn9CjkDH0Z12D4ElWCMeedQXqQyMFTykxu0MpIriqZ1pX5ke1gJ4Y3ROu9jIYGnFPZdc3PToVZpMiKutVxec0gPVuFBlQ-GFp3tYzCMKRsfTz3PT4MV5GPhnmDZlR-zxYjQGyNlRU5MkazMz8yaAoLnaq-4KlteQIEpkOmULPD1pl_3HWpJckMFlitoYWNF9TKHhgPvIhjU2uo0Rv3Wzzz1AveH9hUZi177htmhaAe6NpG7qkG4aUE7d86WcDkL23vnRTGA-V-z9gw
我们在登陆查看,就只能看到一个默认的default的名称空间,其他的都看不到。因为之前绑定的是default名称空间的管理权限。当然,这里也可以使用域名加端口进行访问。
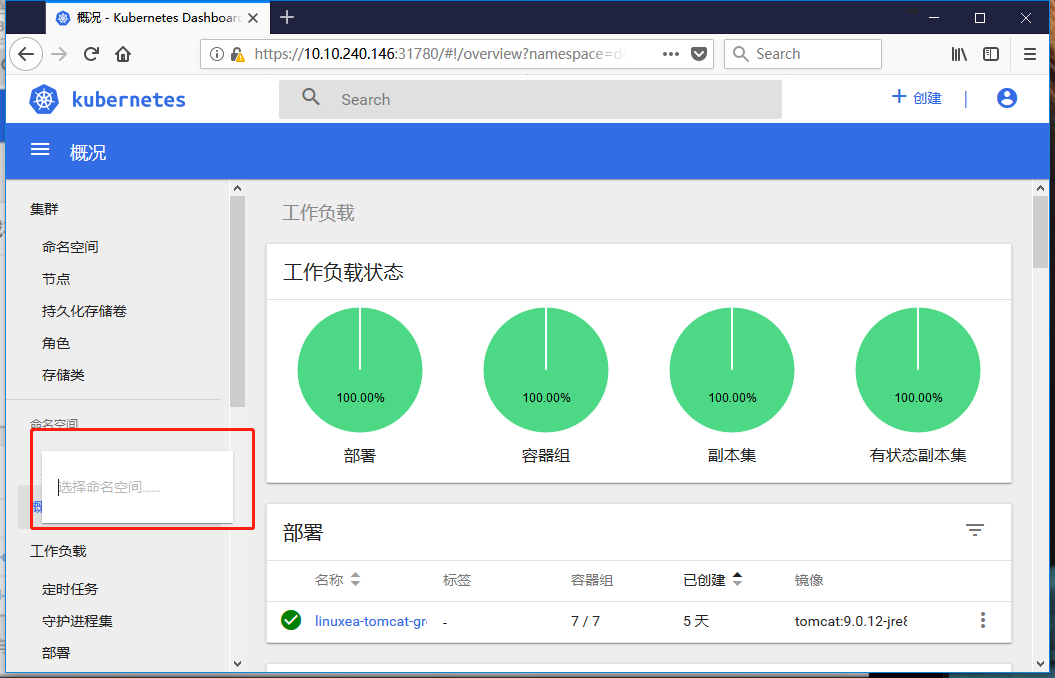
kubeconfig认证#
此刻如果不希望使用token认证,而是希望通过config文件认证,就需要创建一个config文件
但是仍然需要创建serviceaccount,并且创建rolebinding或者clusterrole绑定,并且配置,在配置中还需要将此前的token字段解码放进去,也就是说使用config文件认证就需要先创建token认证,在token认证之上做的config认证。而后完成通过提交一个配置文件来完成登陆验证。
1,配置config#
生成kubeconfig。在/etc/kubernetes/pki/下,并且使用kubernetes的ca证书来做k8s的认证。另外存放到/root/linuxea-default-admin.conf
[marksugar@linuxea pki]# kubectl config set-cluster kuberntes --certificate-authority=./ca.crt --server="https://10.10.240.161:6443" --embed-certs=true --kubeconfig=/root/linuxea-default-admin.conf
Cluster "kuberntes" set.
[marksugar@linuxea pki]# kubectl config view --kubeconfig=/root/linuxea-default-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://10.10.240.161:6443
name: kuberntes
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
2,配置credentials#
credentials是可以使用证书和token认证的,这里使用token进行认证
- 将之前的kube-system dashboard-admin-token-vc7cv中token来创建credentials。这段做了base64 -d的解码
[marksugar@linuxea ~]# kubectl get secret -n kube-system dashboard-admin-token-vc7cv -o jsonpath={.data.token} |base64 -d
生成credentials,并且使用此前生成好的token,将这个token包含进来
- dashboard-admin-token名称并不作为登陆的用户名称,创建serviceaccount的dashboard-admin名称才是真正与api server认证的名称
[marksugar@linuxea pki]# kubectl config set-credentials dashboard-admin-token --token=$(kubectl get secret -n kube-system dashboard-admin-token-vc7cv -o jsonpath={.data.token} |base64 -d) --kubeconfig=/root/linuxea-default-admin.conf
[marksugar@linuxea pki]# kubectl config view --kubeconfig=/root/linuxea-default-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://10.10.240.161:6443
name: kuberntes
contexts: []
current-context: ""
kind: Config
preferences: {}
users:
- name: dashboard-admin-token
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdmM3Y3YiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZGZlNWNkYWYtYzlmMy0xMWU4LWE4YWItODg4ODJmYmQxMDI4Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.qcPhHAkyW0k5gdkkDaTD-DVxRcrZ5Ml_Kcxw0mZIYlJWME_1Wu1_i4B9jE1RcwKDZHV0ND8jpN91oUg1Ac8O6X8VwsfpFw1HzcBv7Te46L4_Z2NjIBuf6cPngkHx1Ija08_BLUd--i3E9cJrTsrqaZojr1JO4ZTHifU7K6cKpGUmbvbYjkIASzj8onT2988znkjp13bvdx7YF3hrKMg4jeDFbR-yMPEwXadgiY0IHArekzLuL37KiRVGgEubuqZFy7fkBPiSQGWc9ecl5dwhmhfofHm7WuKlf4Lvwyz3ivGqPFuoKk0AMmAME3ULOO7INaTlRQkSGJs-bdWl7y-eIg
3,配置context#
配置context,指明集群--cluster=kuberntes,指定dashboard-admin-token用户到/root/linuxea-default-admin.conf配置文件
[marksugar@linuxea pki]# kubectl config set-context dashboard-admin-token@kubernetes --cluster=kubernetes --user=dashboard-admin-token --kubeconfig=/root/linuxea-default-admin.conf
Context "dashboard-admin-token@kubernetes" created.
[marksugar@linuxea pki]# kubectl config view --kubeconfig=/root/linuxea-default-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://10.10.240.161:6443
name: kuberntes
contexts:
- context:
cluster: kubernetes
user: dashboard-admin-token
name: dashboard-admin-token@kubernetes
current-context: ""
kind: Config
preferences: {}
users:
- name: dashboard-admin-token
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdmM3Y3YiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZGZlNWNkYWYtYzlmMy0xMWU4LWE4YWItODg4ODJmYmQxMDI4Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.qcPhHAkyW0k5gdkkDaTD-DVxRcrZ5Ml_Kcxw0mZIYlJWME_1Wu1_i4B9jE1RcwKDZHV0ND8jpN91oUg1Ac8O6X8VwsfpFw1HzcBv7Te46L4_Z2NjIBuf6cPngkHx1Ija08_BLUd--i3E9cJrTsrqaZojr1JO4ZTHifU7K6cKpGUmbvbYjkIASzj8onT2988znkjp13bvdx7YF3hrKMg4jeDFbR-yMPEwXadgiY0IHArekzLuL37KiRVGgEubuqZFy7fkBPiSQGWc9ecl5dwhmhfofHm7WuKlf4Lvwyz3ivGqPFuoKk0AMmAME3ULOO7INaTlRQkSGJs-bdWl7y-eIg
4,配置use-context#
将dashboard-admin-token@kubernetes作为/root/linuxea-default-admin.conf文件中的当前用户
[marksugar@linuxea pki]# kubectl config use-context dashboard-admin-token@kubernetes --kubeconfig=/root/linuxea-default-admin.conf
Switched to context "dashboard-admin-token@kubernetes".
[marksugar@linuxea pki]# kubectl config view --kubeconfig=/root/linuxea-default-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://10.10.240.161:6443
name: kuberntes
contexts:
- context:
cluster: kubernetes
user: dashboard-admin-token
name: dashboard-admin-token@kubernetes
current-context: dashboard-admin-token@kubernetes
kind: Config
preferences: {}
users:
- name: dashboard-admin-token
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tdmM3Y3YiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZGZlNWNkYWYtYzlmMy0xMWU4LWE4YWItODg4ODJmYmQxMDI4Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.qcPhHAkyW0k5gdkkDaTD-DVxRcrZ5Ml_Kcxw0mZIYlJWME_1Wu1_i4B9jE1RcwKDZHV0ND8jpN91oUg1Ac8O6X8VwsfpFw1HzcBv7Te46L4_Z2NjIBuf6cPngkHx1Ija08_BLUd--i3E9cJrTsrqaZojr1JO4ZTHifU7K6cKpGUmbvbYjkIASzj8onT2988znkjp13bvdx7YF3hrKMg4jeDFbR-yMPEwXadgiY0IHArekzLuL37KiRVGgEubuqZFy7fkBPiSQGWc9ecl5dwhmhfofHm7WuKlf4Lvwyz3ivGqPFuoKk0AMmAME3ULOO7INaTlRQkSGJs-bdWl7y-eIg
而后将/root/linuxea-default-admin.conf 文件复制到需要登陆的主机,即可使用文件登陆